How to Filter Duplicate Content from 2T Dictionary Large Text
2025-03-17 12:01:01
Cracking RAR/ZIP/Office Passwords Online
2025-02-03 13:01:24
Tutorial on cracking passwords using GPU graphics card performanc
2024-12-25 15:48:35
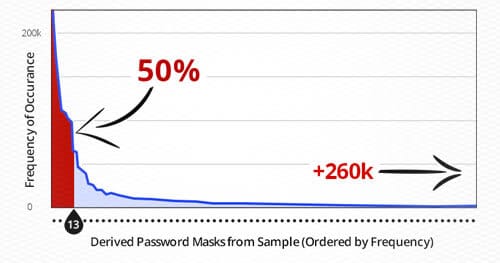
How to Improve the Success Rate of Password Cracking Technology
2024-12-25 12:44:09
Hashcat claims to be the world's fastest password cracking tool.
2024-12-24 20:36:31
Experience sharing of hashcat using GPU acceleration to improve d
2024-12-24 20:19:23
Hashcat tutorial on cracking mode parameter settings
2024-12-24 20:05:32
Hashcat is a password explosion artifact
2024-12-24 17:32:08
Hashcat usage method and technical sharing
2024-12-24 12:26:55