How to use hashcat software to explode various hashes
2024-12-24 12:12:10
Zero, background knowledge
1. hash function
The hash function is a general term for a class of functions, the input of this kind of function is arbitrary binary data, and the output is binary data of fixed length, this kind of function has the following characteristics:
Unidirectionality: It is simple and fast to calculate an output from an input, while it is mathematically not feasible to reverse an input from an output
Collision constraints: It is extremely difficult to find two different inputs with the same output
Functions that meet these characteristics can be called hash functions. Taking a certain data as the input of the hash function, the output is calculated, and this output is customarily called the hash value of the data.
One of the functions of the hash function is to store the password securely, not directly save the password (that is, the password is not stored in plaintext), but save the hash value of the password, and only need to calculate the hash value of the entered password again, and compare it with the hash value of the saved password to know whether the password is correct. Due to the unidirectional nature of the hash function and the collision constraint, it is difficult for an attacker to know the password itself even if it obtains the hash value of the password.
2.hashcat
If an attacker gets the hash value of the password, is there really no way to know the password itself? Of course not, although it is not mathematically feasible to directly calculate the password itself from the hash value of the password, but we know that the output of the hash function is simple and fast to calculate from the input. The operation of constantly trying to get the input corresponding to the hash value is called blasting.
Based on this line of thinking, HashCat was born, and it is said that HashCat was born to prove that it is very simple to blast hash. hashcat claims to be the world's fastest hash blasting tool, and it even supports GPUs and FGPAs if you have them.
hashcat is not only fast, but also professionally supports more than 200 hash functions, using the following commands:
hashcat --help
You can see a list of all hash functions supported by hashcat, and I won't post them here if there are too many.
Hashcat is installed in Kali by default and can be used directly. But my Kali is installed in VirtualBox and I always feel that the virtual machine will be slower, so I want to use hashcat in the physical host. Download hashcat from the official website of hashchat, as of now, the latest version is v3.5.0, released on 2017.04.05, it can be seen from the update date that hashchat is vibrant. Eliminate the trouble of compilation, download the binary package directly, only 2.7M, which is very small compared to games that often cost tens of G.
After the download is complete, unzip the hashcat and see the following:
hashcat32.bin
hashcat32.exe
hashcat64.bin
hashcat64.exe
Such files are executable files in Linux and Windows under 32-bit and 64-bit respectively, and you can choose one of them according to the situation of your computer. I chose hashcat64.bin, and for the sake of pretty, add a line to the ~/.bashrc file:
alias hashcat='hashcat64.bin的路径'
After saving, re-open the virtual terminal to make the ~/.bashrc file take effect, so that no matter where you are, you can directly enter the hashcat command without switching directories or entering ugly "64.bin", as shown in the figure below.

Okay, now you can start blasting all kinds of hashes with hashcat.
1. Blasting MD5
MD5 is probably one of the most well-known and widely used hash functions. First, use Python to generate a few md5 values for blasting, and the code is as follows:
import hashlib passwords = ['123123', 'bond007', 'xxxxxx', '*H@&(NT*@BR#^'] for password in passwords: md5 = hashlib.md5() md5.update(password) print md5.hexdigest()
The above code calculates the hash values of the four strings respectively, and the output result is:
4297f44b13955235245b2497399d7a93 cbdb7e2b1ed566ceb796af2df07205a3 dad3a37aa9d50688b5157698acfd7aee d77db958c179bbffae04b2b908b75c26
Save the output in the file md5.hash with one HAHS value per line. Then use hashcat to blast these hash values, and the command is as follows:
hashcat -w 3 -a 0 -m 0 --remove -o md5.out md5.hash wordlist.dic
The -w parameter is used to specify the working mode, and there are four types, as shown in the following table:
| N | Performance | Runtime | Power Consumption | Desktop Impact |
|---|---|---|---|---|
| 1 | Low | 2 ms | Low | Minimal |
| 2 | Default | 12 ms | Economic | Noticeable |
| 3 | High | 96 ms | High | Unresponsive |
| 4 | Nightmare | 480 ms | Insane | Headless |
The parameter -a is used to specify the attack mode, the meaning of 0 is direct and continuous, that is, it is blasted with a password dictionary, and there are five values of -a, as shown in the following table:
| N | Mode |
|---|---|
| 0 | Straight |
| 1 | Combination |
| 3 | Brute-force |
| 6 | Hybrid Wordlist + Mask |
| 7 | Hybrid Mask + Wordlist |
-m is used to specify the hash value to be blasted, 0 indicates that the hash function is md5, and the other values are shown in the following table:
| N | Name | Category |
|---|---|---|
| 0 | MD5 | Raw Hash |
| 300 | MySQL4.1/MySQL5 | Database Server |
| 1000 | NTLM | Operating Systems |
| 1800 | sha512crypt $6$, SHA512 (Unix) | Operating Systems |
| 2611 | vBulletin < v3.8.5 | Forums, CMS, E-Commerce, Frameworks |
This table is too long, I will only show a few hash functions involved in this article, and you can see all of them with the argument –help.
The argument –remove means that if a hash value is successfully exploded, it will be removed from md5.hash.
The parameter -o is followed by a file name indicating where the blasting results are saved.
The last two parameters, md5.hash and wordlist.dic, are the hash value to be blasted and the password dictionary, respectively. The contents of md5.hash have been calculated by Python, if you don't have a proper password dictionary at hand, you can use the command:
wget -O wordlist.dic https://samsclass.info/123/proj10/500_passwords.txt
Download one. Now that everything is done, press enter, and the result is gorgeously error :(
clGetPlatformIDs(): CL_PLATFORM_NOT_FOUND_KHR
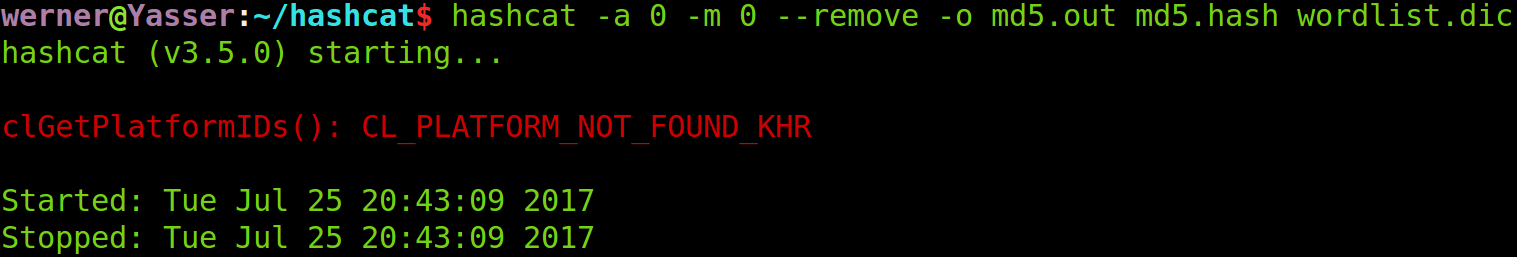
Probably there is a lack of some runtime environment, then install it. I installed these things in total:
sudo apt-get install gcc make p7zip-full git lsb-core wget http://registrationcenter-download.intel.com/akdlm/irc_nas/9019/opencl_runtime_16.1.1_x64_ubuntu_6.4.0.25.tgz tar -xvf opencl_runtime_16.1.1_x64_ubuntu_6.4.0.25.tgz cd opencl_runtime_16.1.1_x64_ubuntu_6.4.0.25 sudo ./install.sh
If the network speed is good, it will be safe in a short time, and the first command will report an error:
/sbin/ldconfig.real: /usr/lib/nvidia-375/libEGL.so.1 is not a symbolic link /sbin/ldconfig.real: /usr/lib32/nvidia-375/libEGL.so.1 is not a symbolic link
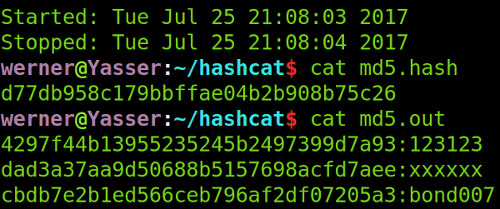
But it doesn't seem to affect anything, so it's better to ignore it. After installing these, press enter again, run the command that originally reported the error, and found that there was no error again, and in an instant, the execution was completed. After the command is executed, check the contents of the file md5.hash and md5.out, and find that there is only one hash left in the md5.hash, and the three hashes that have been successfully blasted have been transferred to the file md5.out, and the three hash values and their original values are in md5.out, as shown in the following figure:
二、爆破Windows7登录密码hash
Windows的登录密码的hash值保存在SAM文件中,SAM是"security account manager"的首字母缩写。 通常,它位于
C:\windows\system32\config\SAM
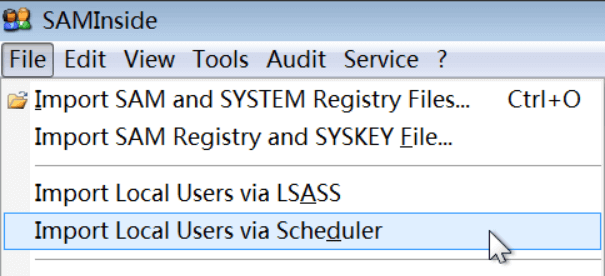
SAM files are protected by Windows and cannot be read directly, requiring the help of a tool such as SAMInside. Find a Windows 7 virtual machine, create a new admin user named hashcat, set a password, download and decompress SAMInside in Windows 7, run it with administrator privileges, and then click File->Import Local Users vis Scheduler, as shown in the following figure:
After that, SAMInside may be "unresponsive", but it doesn't matter, wait a few seconds patiently, and SAMInside will read the hash we want, as shown in the image below:
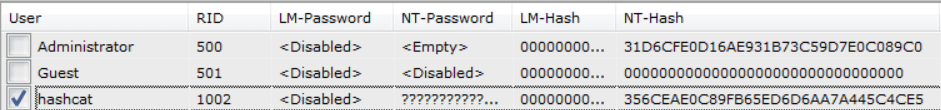
Select the user "hashcat" we want to blast the password, press Ctrl+5 to copy NT-hash, then go back to Ubuntu with hashcat installed, and use the following command to save the copied hash value to the file win7.hash:
echo 356CEAE0C89FB65ED6D6AA7A445C4CE5 > win7.hash
NT-hash便是Windows7保存登录密码使用的hash函数,接着用如下命令爆破NT-hash:
hashcat -w 3 -a 0 -m 1000 --remove -o win7.out win7.hash wordlist.dic
After a while, the execution is completed, check the win7.out file, and find that the blasting is successful, and the login password of user hashcat is rush2112:
werner@Yasser:~/hashcat$ cat win7.out 356ceae0c89fb65ed6d6aa7a445c4ce5:rush2112
For more information on how to get a SAM file, please refer to "How to Export Windows Hash Series I". The following is a record of my process of reading the SAM file in the virtual machine Windows 7.
If it is a physical machine, use Win PE to start the machine and read the SAM file on the disk. Mine is a virtual machine, and I can read the files in the virtual disk by mounting the virtual disk files to the file system. The virtual machine I'm using is VirtualBox, which can be done with the command vdfuse. If you don't have vdfuse, you need to install virtualbox-fuse first:
sudo apt-get install virtualbox-fuse
You can also download the virtualbox-fuse installation package to install it yourself.
After the installation is complete, you will have the vdfuse command, and you can start the virtual disk mapping and mounting:
mkdir -p ~/vmdisk sudo vdfuse -t VMDK -f Win7Pro32.vmdk ~/vmdisk/
执行完这步后查看~/vmdisk目录,其中有三个文件:EntireDisk、Partition1和Partition2,新建目录:
mkdir -p ~/vmdisk_en mkdir -p ~/vmdisk_1 mkdir -p ~/vmdisk_2
用mount命令分别挂载EntireDisk、Partition1和Partition2这三个文件:
sudo mount ~/vmdisk/EntireDisk ~/vmdisk_en sudo mount ~/vmdisk/Partition1 ~/vmdisk_1 sudo mount ~/vmdisk/Partition2 ~/vmdisk_2
Found that the EntireDisk mount failed, the content in Partition1 is not what I want, and in Partition2 is the file in the Windows 7 virtual machine, exactly what I wanted. Copy out our target SAM file from the vmdisk_fs:
cp ~/vmdisk_2/Windows/System32/config/SAM ./
By the way, copy the SYSTEM file as well:
cp ~/vmdisk_2/Windows/System32/config/SYSTEM ./
Looking at the content of the SAM file, as shown in the figure below, it turned out to be not a plain text file, and it was really in the style of Windows,
Well, although we successfully opened the SAM file, we still don't get the hash, what should we do next? The only way to parse the contents of the SAM file is to use a tool. Put both the SAM file and the SYSTEM file into Kali and run the command:
samdump2 -o sam.hash SYSTEM SAM
Then look at sam.hash, and you can also see the hash value of each user's login password. Each line in the sam.hash file is a user, and each line is formatted:
用户名称:RID:LM-hash值:NTLM-hash值
Note that this format is the output format of the samdump2 command, not the "Hash password format under Windows".
3. Blasting the Linux login password hash
First of all, you have to have a computer running a Linux system, which is easy to say, a virtual machine is fine. Then, run the following command to add a new user and set a password for our blasting purposes:
sudo adduser justforfun
In Linux, the hash value of the user's login password is stored in the file /etc/shadow (note: not /etc/passwd), run the following command to view the hash value of the login password of the new user:
test@test-VirtualBox:~$ sudo tail -n 1 /etc/shadow justforfun:$6$0fokwg59$6hpMS5dM9wDT/42DDoSD0i0g/wHab50Xs9iEvVLC3V20yf1kRmXZHGXCM0Efv6XU69hdgMZ4FwaMzso4hQaGQ0:17373:0:99999:7:::
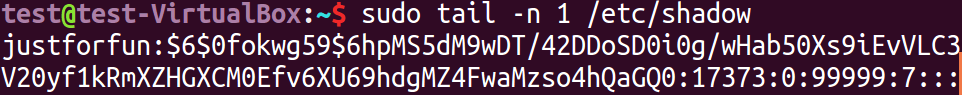
The tail command is used to read the last few lines of a file, the default is 10 lines, and the number of lines is specified with the parameter -n. The user we just created is naturally on the last line, so we use tail -n 1 to read. The result is that the data is split with ":", the first part is the username "justforfun", the second part is the hash value of the password, and the other parts are not to be concerned about in this article. Let's focus on the second part.
开头的“$6$”指所用hash函数的类型为SHA-512,除“$6$”外,在linux中,“$1$”指MD5, “$2a$”指Blowfish, “$2y$”指Blowfish(correct handling of 8-bit chars), “$5$”指SHA-256,详情参见维基百科:passwd。 此外,文件/etc/login.defs也对hash算法有所说明。
The part "0fokwg59" that starts with "$6$" and precedes the next "$" is salt. What is Salt? Baidu knows CNB2009 answer to the question "What is MD5 salt value" is simple and easy to understand:
To put it simply, it is a means to make the same password have different hash values, which is salting. MD5 itself is irreversible, but there are many databases on the Internet that support anti-query, if the user password database is accidentally leaked, hackers can obtain the user's password through anti-query, or brute-force cracking of the frequently occurring hash code in the database (i.e., used by many people) (because it is usually a weak password). The salt value is an extra random value added in the password hash process, for example, my ID is crazy ω pour (4) ゞ, the password is 123456, when stored in the database, you can hash the string "123456/mad ω pour (4) ゞ", and when verifying the password, it is also verified with the string "(password to be verified)/mad ω pour (4) ゞ". In this way, when there is another dumb password that is 123456, it can still construct a different hash value and successfully verify it. At this point, my ID is used as a salt value to hash the password. So... The role of salt is to reduce the cost of database leakage. If your RP is very good and you guess my password is 123456, I can't stop you
This answer is for md5, as are the other hash functions. The part after the salt is the hash value. Now copy the entire second part into the file linux.hash, the contents of linux.hash should be:
$6$0fokwg59$6hpMS5dM9wDT/42DDoSD0i0g/wHab50Xs9iEvVLC3V20yf1kRmXZHGXCM0Efv6XU69hdgMZ4FwaMzso4hQaGQ0
Then blast the Linux login password hash with the following command:
hashcat -w 3 -a 0 -m 1800 --remove -o linux.out linux.hash wordlist.dic
After a few moments, the blasting is complete, see the results:
werner@Yasser:~/hashcat$ cat linux.out $6$0fokwg59$6hpMS5dM9wDT/42DDoSD0i0g/wHab50Xs9iEvVLC3V20yf1kRmXZHGXCM0Efv6XU69hdgMZ4FwaMzso4hQaGQ0:4321
It can be seen that the blasting was successful.
四、爆破Mysql登录密码hash
First of all, there has to be Mysql. I happen to have it in my virtual machine. Baidu knows that the hash value of the login password of Mysql is stored in the file user.MYD. File user. And where is MYD? I don't know, so I'll look for it:
test@test-VirtualBox:~$ sudo find / -name user.MYD /var/lib/mysql/mysql/user.MYD
找到了,是在/var/lib/mysql/mysql/user. MYD,查看该文件内容:
sudo cat /var/lib/mysql/mysql/user.MYD
It's not a plain text file, it doesn't matter much, but you can see that the hash value of the user's root login password is:
6B825255FB466413D6B1B724644E23428C94BBCB
Save this value to the mysql.hash file and blast the Mysql login password hash with the following command:
hashcat -w 3 -a 0 -m 300 --remove -o mysql.out mysql.hash wordlist.dic
After a few moments, the blasting is complete, see the results:
werner@Yasser:~/hashcat$ cat mysql.out 6b825255fb466413d6b1b724644e23428c94bbcb:viper
It can be seen that the blasting was successful.
5. Blasting the Discuz! forum password
Discuz! is a well-known php forum program in China, and it is extremely widely used. Now let's blast the hash value of the Discuz! user password. The first thing you have to find is the hash value, where do you find it? From the Discuz!, of course.
But where is the database of Discuz!? Here's how I solved it, downloaded the latest version of the Discuz! source code from its official website, ran the installation, and got the Discuz! database
The default database of Discuz! is called ultrax, and the hash value of the login password is stored in the pre_ucenter_members table, "pre_" is the default prefix, which can be changed during installation, and "ucenter_members" does not change. Use the following SQL statement to query the hash value of the login password:
select password,salt from pre_ucenter_members;
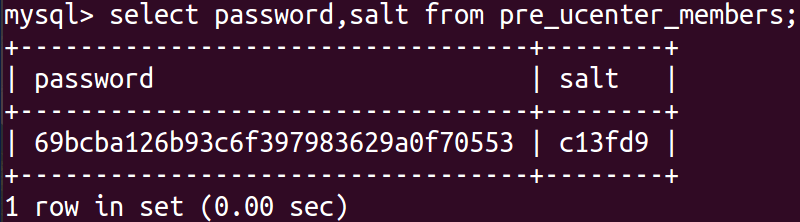
Save the hash and salt values to the file:
echo 69bcba126b93c6f397983629a0f70553:c13fd9 > discuz.hash
The hash value and the salt value are in the same line, separated by ":". Finally, blast the Discuz login password hash with the following command:
hashcat -w 3 -a 0 -m 2611 --remove -o discuz.out discuz.hash wordlist.dic
After a few moments, the blasting is complete, see the results:
werner@Yasser:~/hashcat$ cat discuz.out 69bcba126b93c6f397983629a0f70553:c13fd9:winter
It can be seen that the blasting was successful.
6. Big Dictionary Test
Up to now, we have used a small dictionary of only 500 words, and it only takes a few moments each time to successfully blast all kinds of hashes, isn't it strange? This is because I deliberately set a weak password in the dictionary to practice using hashcat, otherwise it would be very bad to not be able to burst out. In reality, there is no such good luck. Let's randomly calculate the md5 value of a not-so-weak cipher, blast it with a big dictionary, try your luck on the one hand, and see how fast Hashcat can be on the other.
First, calculate the MD5 value:
import hashlib
md5 = hashlib.md5()
md5.update("werner123456!!!")
print md5.hexdigest()The output is:
b17133f9abff287ed0546c1af2b171f7
Then select a 10.5G dictionary with 940 million passwords and start blasting:
hashcat -w 3 -a 0 -m 0 --remove -o big.out b17133f9abff287ed0546c1af2b171f7 big.dic
Note that if there is only one hash value, it can be written directly in the command line argument instead of saving it in a file. Start blasting before going to bed, and when you get up the next day to see the results, you find:
Started: Wed Jul 26 22:55:27 2017 Stopped: Wed Jul 26 23:02:28 2017
It only took 7 minutes! I thought it would take 7 hours, which was 60 times faster than I expected! It's a bit of a pity that there was no successful blasting out of the hash value, it seems that "werner123456!!" Not in the password dictionary. It seems that I need to prepare a 100G password dictionary, but it is inconvenient to save and transfer such a large dictionary, is there no other way? Of course there is, remember the attack mode? We've been using the "Straight" mode, so let's look at a few others.
7. Summary
Using hashcat to blast hash, the first is to find the hash, different systems, different software, the location of the hash is different, you need to find out the hash value accurately; The second is to correctly judge the hash type, determine whether the hashcat supports this kind of hash, and select the right -m parameter, otherwise it is almost impossible to succeed; The third is that the password dictionary is good, and whether it can be successfully blasted in the end depends on the dictionary. Although the bigger the password dictionary is not the better, but the bigger is always better, and hashcat is also known for its speed, and a large dictionary is not a problem for hashcat. Here is a good dictionary to record: the collection of previous leak doors + commonly used weak password dictionaries.7z and the decompression password is: anywlan. In addition, if you have collected a lot of small dictionaries, you can merge, sort, and deduplicate the small dictionaries to get a large dictionary for hashcat blasting. If the small dictionaries are in the same directory, you can use a single command:
cat * | sort | uniq > Merge.dic
What if small dictionaries were organized by category and distributed across multiple levels of contents? Obviously not enough to use the cat command, but in fact, you only need one command, assuming that the small dictionaries are stored in the directory MyDictionary, the command can be written like this:
find ./MyDictionary -type f -exec cat {} \; | sort | uniq > Merge.dic